Security
HomeSecurity
-
Jan 6, 2021
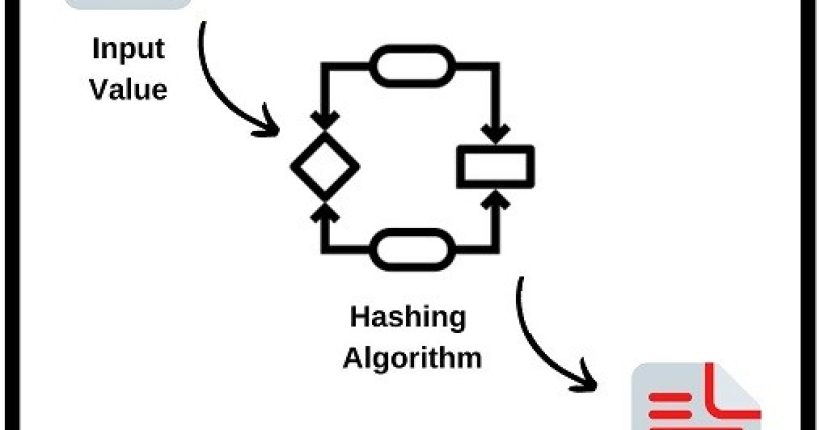
In this post we will learn what is hashing or what is a hash? We will try to explain hash...
-
Dec 1, 2020
What is Multifactor Authentication? As you know password are one of the most used security mechanisms to secure a device....
-
Nov 5, 2020
Control Plane Policing (CoPP) is one of the mechanisms used for Control Plane defence against the Network Attacks that is...
-
Aug 24, 2020
Cyber Security is one of the most popular case of today’s information technology World. With the development of the information...
-
Aug 23, 2020
Cyber Security is a popular area of Information Technology (IT). Especially in recent years, with the development of the technology...
-
Mar 6, 2020
Cyber Attacks, Network Attacks, Threats, Vulnerabilitis and Mitigation There are various Network Attacks and various ways to prevent yourself...
-
Sep 18, 2019
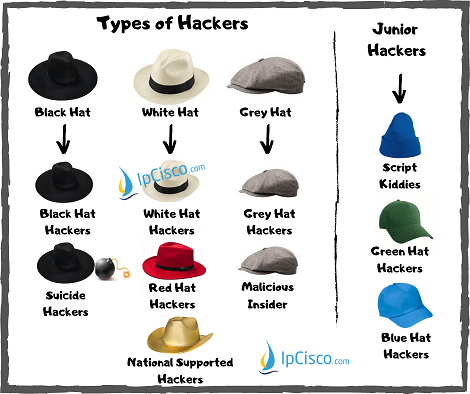
A Hacker is a highly skilled person on Cyber Security, Computer Systems and Networks. In other words, they are the...
-
Apr 8, 2019
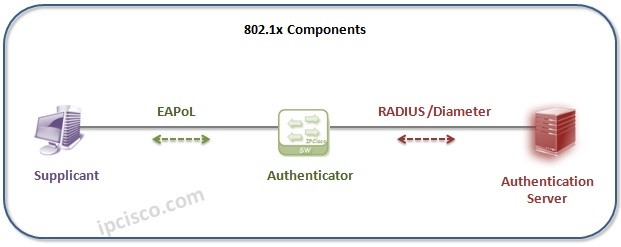
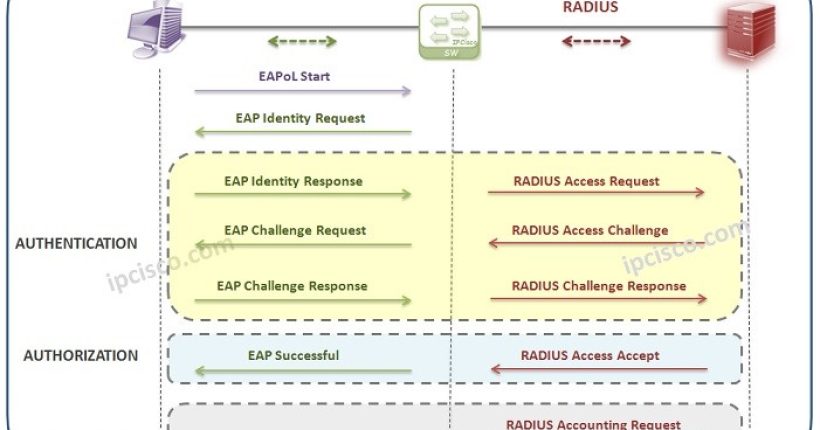
EAPoL is the abbreviation of Extensible Authentication Protocol over LAN. EAPoL (Extensible Authentication Protocol over LAN) is a network authentication...
-
Apr 8, 2019
802.1x (Port Based Network Access Control) 802.1x is a LAN Security Mechanism that provides port based access control in the...
-
Apr 8, 2019
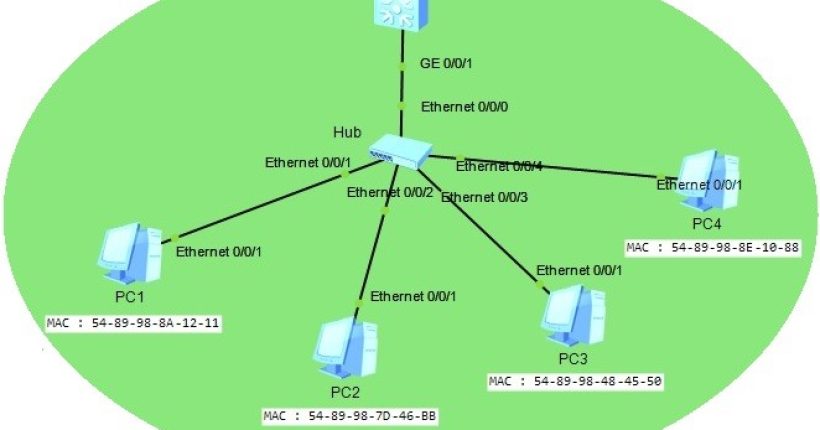
In this Huawei Port Security Configuration Example, we will configure Port Security on a Huawei switch. For our Huawei Port...
Popular posts
Cisco Interview Questions
June 30, 2025
CCNA
Network Operating System
March 13, 2025
Basic
CCNA Minor Update! | CCNA 200-301 v1.1
July 9, 2024
Basic
Cisco Packet Tracer Overview
June 26, 2024
CCNA
Sign up to receive our latest updates
[mc4wp_form id=3101]
Get in touch
Call us directly?
+1 234 567 8910
Address
Howard Street, San Francisco
contact@eduma.com