Blog
HomeBlogPage 34
-
Apr 3, 2015
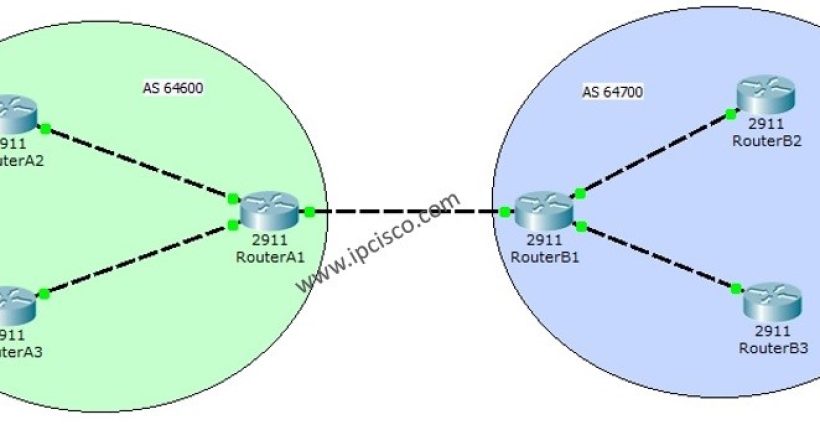
Packet Tracer BGP Configuration Example To understand BGP (Border Gateway Protocol) better, we will make a basic Packet Tracer BGP...
-
Apr 1, 2015
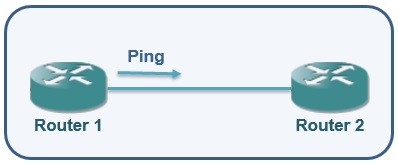
Ping Command and Ping Command Options Whenever other engineers see network engineers during troubleshooting, they think that, network engineers only...
-
Mar 30, 2015
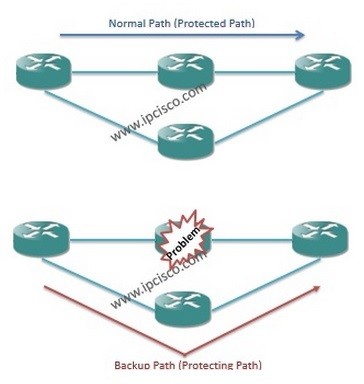
Both One-to-One and Facility Backup can protect different network elements. And these can be achieved by two ways: – Node...
-
Mar 30, 2015
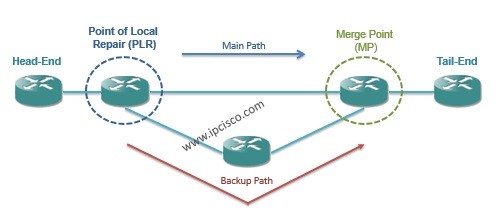
The goal of the protection is minimizing the down time. To do this, protection must be done near to the...
-
Mar 30, 2015
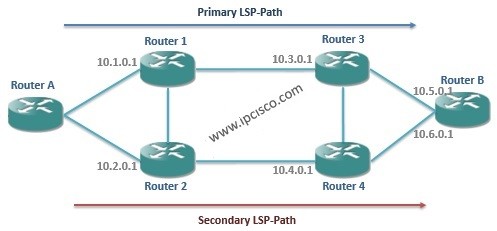
As we say in the following articles, while using Secondary LSP-Paths, sharing links between Primary and Secondary LSP-Paths must be...
-
Mar 30, 2015
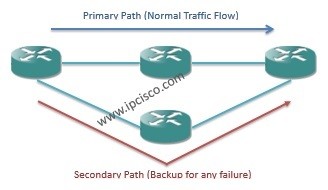
There are some different types traffic protections. In general we can divide these types into two groups. End-to-end Protection and...
-
Mar 30, 2015
As you know, we can prioritize some of the traffic with MPLS-TE because of their nature. The high priority can...
-
Mar 30, 2015
After the link failure in MPLS network, there are some actions need to be done orderly for MPLS recovery. This...
-
Mar 30, 2015
What Happens After the Failure Recovered By Fast Reroute (FRR) ? After detecting the failure in an MPLS network, in...
-
Mar 30, 2015
In the Alcatel-Lucent 7750 Service Routers, we can verify the Secondary LSP-Path configuration with the following commands. Verifying secondary LSPs...
Popular posts
Cisco Interview Questions
June 30, 2025
CCNA
Network Operating System
March 13, 2025
Basic
CCNA Minor Update! | CCNA 200-301 v1.1
July 9, 2024
Basic
Cisco Packet Tracer Overview
June 26, 2024
CCNA
Sign up to receive our latest updates
[mc4wp_form id=3101]
Get in touch
Call us directly?
+1 234 567 8910
Address
Howard Street, San Francisco
contact@eduma.com