
Cyber Attacks, Network Attacks, Threats, Vulnerabilitis and Mitigation
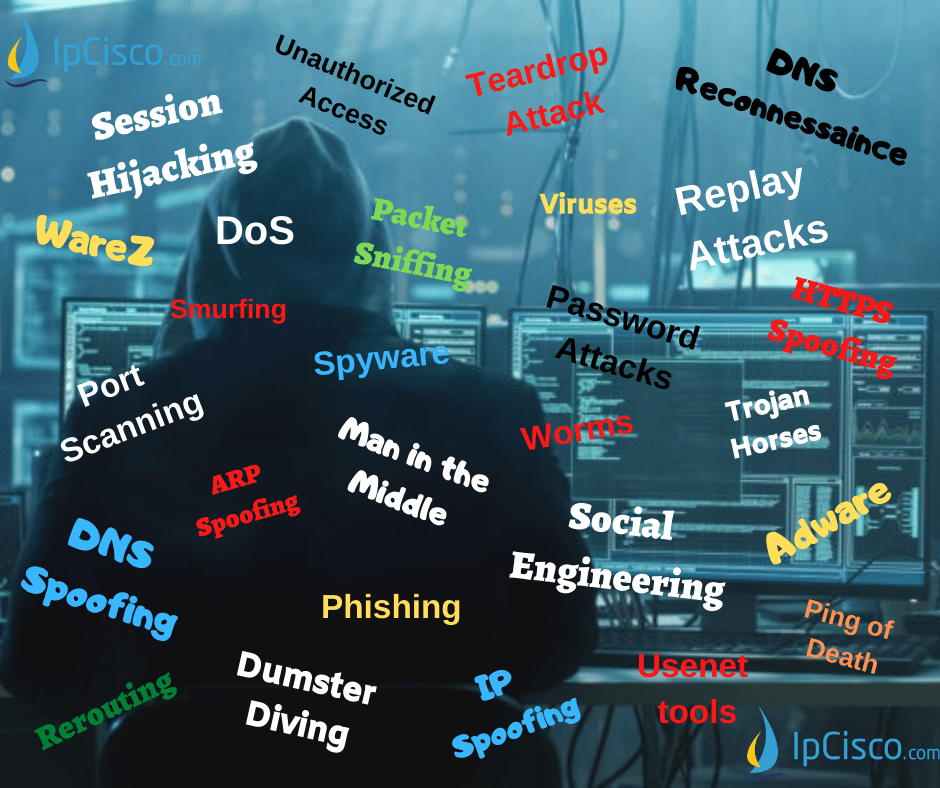
There are various Network Attacks and various ways to prevent yourself from the attackers. In this lesson we will focus what are these Network Attacks, Cyber Attacks. So, what are the types of Network Attacks (Cyber Attacks)?- Denial of Service (DoS) Attack
- TCP SYN Flood Attack
- Ping of Death
- Teardrop Attack
- Smurfing
- Man-in-the-Middle Attacks
- Session Hijacking
- Replay Attacks
- IP Spoofing
- ARP Spoofing
- DNS Spoofing
- HTTPS Spoofing
- Password Attacks
- Malware Attacks
- Viruses
- Worms
- Trojan Horses
- Adware
- Spyware
- Reconnaissance Attacks
- Packet Sniffing
- Port Scanning
- Phishing
- Social Engineering
- Dumster Diving
- Usenet tools
- DNS Reconnessaince
- Other Attacks
- Unauthorized Access
- WareZ
- Rerouting

Denial of Service (DoS) Attacks
Denial of Service (DoS) Attack is a cyber attack type that aims to maket he victim system unusable. There are different types of DoS Attacks according to their type:- Vulnerability DoS Attacks
- Bandwidth Flooding DoS Attacks
- Connection Flooding DoS Attacks
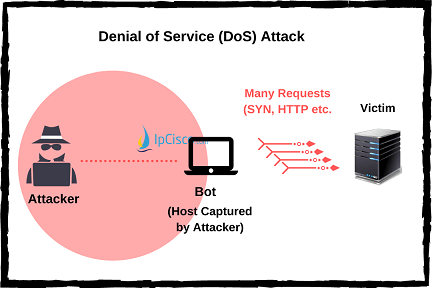 Lastly Connection Flooding DoS Attacks are done with too much half or full open connections. After a while system can not reply to these requests.
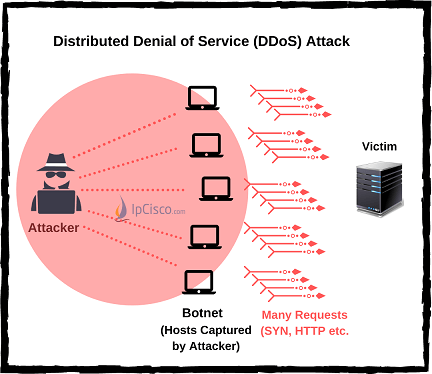
There is also an enhanced version of DoS Attacks. These are DDoS (Distributed DoS) Attacks. With DDOS Attacks, attacker attacks from many devices o the victim device. So, it is difficult to detect the source of this attacks.
By the way let’s also define an important term, Botnet. Botnet is a private computer that has infected form any malicious software and because of this, it is controlled without the victim’s knowledge to do malicious attacks to others. DDoS (Distributed DoS) Attacks are done over such systems.
Lastly Connection Flooding DoS Attacks are done with too much half or full open connections. After a while system can not reply to these requests.
There is also an enhanced version of DoS Attacks. These are DDoS (Distributed DoS) Attacks. With DDOS Attacks, attacker attacks from many devices o the victim device. So, it is difficult to detect the source of this attacks.
By the way let’s also define an important term, Botnet. Botnet is a private computer that has infected form any malicious software and because of this, it is controlled without the victim’s knowledge to do malicious attacks to others. DDoS (Distributed DoS) Attacks are done over such systems.
 There are different namings for specific types of DoS Attacks. These are:
There are different namings for specific types of DoS Attacks. These are:
- TCP SYN Flood Attack
- Ping of Death
- Teardrop Attack
- Smurfing
TCP SYN Flood Attack
TCP SYN Flood Attack is the attack with which attacker sends too much connection request to the target and if it gets reply, attacker never replies back. Waiting for timeout and too much requests fills the victim system queues.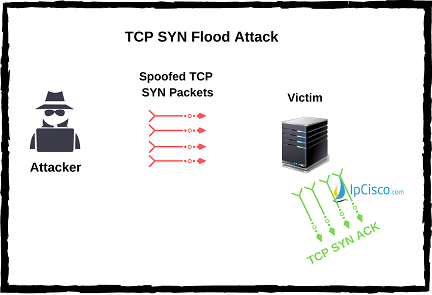 To protect your system form TCP SYN Flood, you can use firewall that stops incoming SYN packets. Another proactive solution is increasing the size of the connection queue and decreasing the connection timeout value.
To protect your system form TCP SYN Flood, you can use firewall that stops incoming SYN packets. Another proactive solution is increasing the size of the connection queue and decreasing the connection timeout value.
Ping of Death
Ping of Death is the attack type that sends ping packet to the victim over maximum 65535 value. And before sending this, attacker fragments the packet because this size is not allowed. At the other end, the victim, reassembeles this packet and its buffer crashes.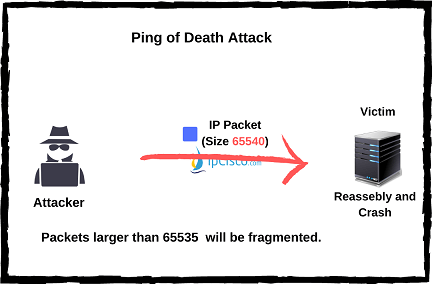 To protect your system from Ping of Death, you can use a firewall and on firewall you can check fragmented packets, if their size is normal or not.
To protect your system from Ping of Death, you can use a firewall and on firewall you can check fragmented packets, if their size is normal or not.
Teardrop Attack
Teardrop Attack is the attack that is done via packet length and fragmentation offset parts. Attacker sends fragmented packets like ping of death. The target, can not reassible this packet because of a bug about TCP/IP fragmentation. The packets overlap and the system crashes.Smurfing
Smurfing is the attacks type that is done via too much ICMP Echo (Ping) and aims to exhaust system resources. With Smurfing, attackers behaves like a victim’S trusted IP address and sends many ICMP Echo messages to a broadcast address. All the devices in this broadcast domain sends ICMP Reply to this ECMP Echos. So, in a short time the system traffic increase and resoruces exhaust.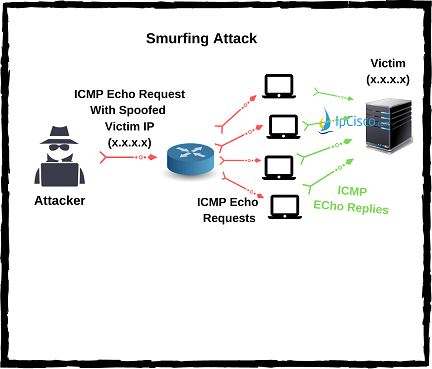
Man-in-the-Middle Cyber Attacks
Man-in-the-Middle Attacks (MiTMs) are one of the most widely used attack types for today’s Cyber Attacks. It is also known as Eavesdropping (Snooping). In a Man-in-the-Middle Attack there are three players. These players are:- Client (Victim)
- Server (The destination that the client are connecting)
- Attacker (The “Man” in the Middle)
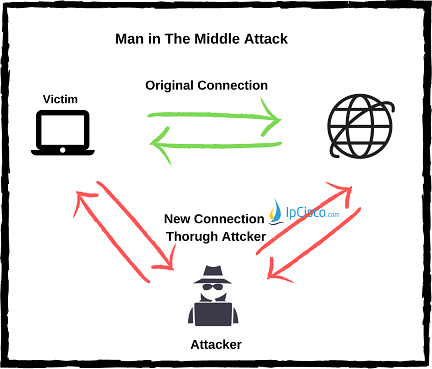 In normal communcation, client connect to the server and the data traffic occurs. But with Man-in-the-Middle Attack, the attacker enters between the Client and the Server. The attacker achieves this with various techniques and because of that victim is unaware of what is going on. He/She thinks that, the connection is still towards the destination. But after a successfull Man-in-the-Middle Attack, the data traffic comes to the attacker’s device not the exact destination.
Man-in-the-Middle Attacks are mainly used for stealing valuable information about the victims. This can be important passwords, banking details or any other secret information. Man-in-the-Middle Attacks can be done on different layers of the well-known OSI Model.
According to its affect type, we can devide Man-in-the-Middle Attacks into two. These Man-in-the-middle Attacks types are :
In normal communcation, client connect to the server and the data traffic occurs. But with Man-in-the-Middle Attack, the attacker enters between the Client and the Server. The attacker achieves this with various techniques and because of that victim is unaware of what is going on. He/She thinks that, the connection is still towards the destination. But after a successfull Man-in-the-Middle Attack, the data traffic comes to the attacker’s device not the exact destination.
Man-in-the-Middle Attacks are mainly used for stealing valuable information about the victims. This can be important passwords, banking details or any other secret information. Man-in-the-Middle Attacks can be done on different layers of the well-known OSI Model.
According to its affect type, we can devide Man-in-the-Middle Attacks into two. These Man-in-the-middle Attacks types are :
- Passive Man-in-the-Middle Attacks (Passive MiTM)
- Active Man-in-the-Middle Attacks (Active MiTM)
- Session Hijacking
- Replay Attacks
- IP Spoofing
- ARP Spoding
- DNS Spoofing
- HTTPS Spoofing
Session Hijacking Cyber Attacks
Session Hijacking is an old cyber attack type with which the attacker receives the traffic between two victioms by capturing the session between them. In this type of attacks, receiver and sender things that they are communication directly with the other end. But, in real, their traffic goes to the attacker.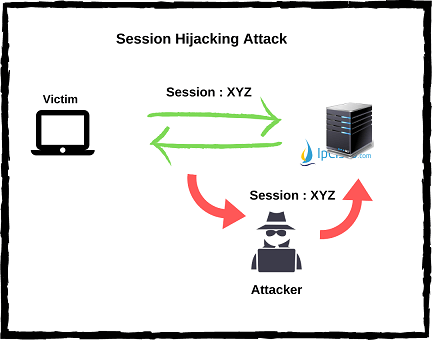
Replay Cyber Attacks
Replay Cyber Attacks are the attacks with which the attacker eavesdrops the traffic between two points, intercepts the traffic and sends requests as he/she is a legitimate user. By doing this, attacker receies the requested data from the destination. Source of the request and the answered destination do not aware of this process. The attacker receives all the information requested. For example if you request a payment with your credentials and if your data is intercepted by the hacker with a replay attack, then, attacker can imitate your request and send it to the destination as he/she is the legitimate user. At the destination, your reuest will processed and your requested money will sent to the attackers account.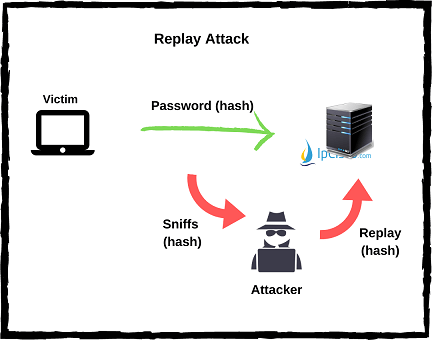
IP Spoofing
IP Spoofing is the process of tricking a victim via trusted IP packets. Here, the attacker sends a modified IP packet that has a trusted IP Source address to the victim host. The host accepts this packet because of the fact that it assumes that it is coming from a secure end. After that, the traffic from the victim goes to the attacker instead of the real trusted destination.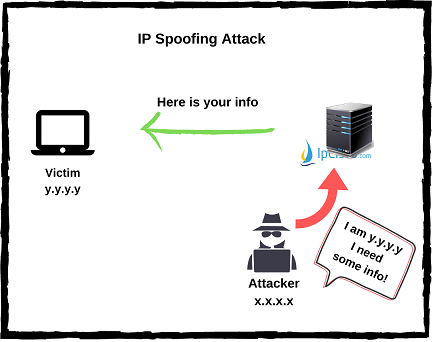 Attackers do IP Spoofing by having a trusted range IP addresses. These IP addresses are in your IP address range. After having such an IP addresses, it is easy to enter your network. So, they acks as they are in your network, they can change configurations, they can send emails, they can do anything like any other user in this network. IP Spoofing is a very dangerous attack.
To protect your company network from IP Spoofing, you can use Access-lists. With Access-lists, you can limited incoming traffic from the outside. But what if this attack is done from inside? So, Access-lists can not be a certain solution for IP Spoofing.
Attackers do IP Spoofing by having a trusted range IP addresses. These IP addresses are in your IP address range. After having such an IP addresses, it is easy to enter your network. So, they acks as they are in your network, they can change configurations, they can send emails, they can do anything like any other user in this network. IP Spoofing is a very dangerous attack.
To protect your company network from IP Spoofing, you can use Access-lists. With Access-lists, you can limited incoming traffic from the outside. But what if this attack is done from inside? So, Access-lists can not be a certain solution for IP Spoofing.
ARP Spoofing
As you know ARP is the protocol tat links IP addresses to MAC addresses. With ARP processes in OSI layer 2, devices in the network learnes their MAC addresses each other and create ARP tables that includes IP-ARP machings. After this learning process, communication is done through this ARP table instead of asking “What is x.x.x.x IP’s MAC?” question every time.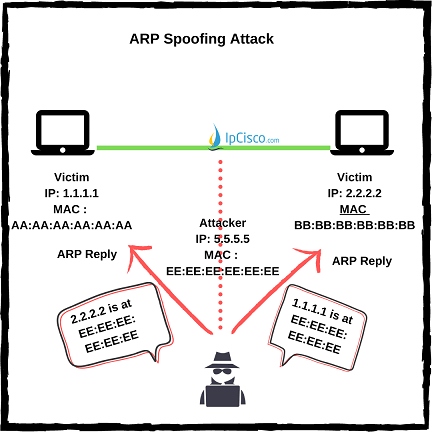 In ARP spoofing, attacker link its own MAC address with a trusted IP address in that network. By doing this, attacker manuplates the ARP table. When the victim host want to send a packet to that IP address according to records of ARP table, it sends the traffic to the attacker. From the victim’s point of view, everything seems normal. ARP table seems secure and it sends the packet according to the ARP table. It do not know that, IP-MAC linking in the ARP table, will send its traffic to the attacker’s malicious device.
In ARP spoofing, attacker link its own MAC address with a trusted IP address in that network. By doing this, attacker manuplates the ARP table. When the victim host want to send a packet to that IP address according to records of ARP table, it sends the traffic to the attacker. From the victim’s point of view, everything seems normal. ARP table seems secure and it sends the packet according to the ARP table. It do not know that, IP-MAC linking in the ARP table, will send its traffic to the attacker’s malicious device.
DNS Spoofing
[sc name=”ContentRMessage”]You May Also Like
-
Jan 6, 2021
In this post we will learn what is hashing or what is a hash? We will try to explain hash...
-
Dec 1, 2020
What is Multifactor Authentication? As you know password are one of the most used security mechanisms to secure a device....
-
Nov 5, 2020
Control Plane Policing (CoPP) is one of the mechanisms used for Control Plane defence against the Network Attacks that is...
-
Aug 24, 2020
Cyber Security is one of the most popular case of today’s information technology World. With the development of the information...
Sign up to receive our latest updates
[mc4wp_form id=3101]
Get in touch
Call us directly?
+1 234 567 8910
Address
Howard Street, San Francisco
contact@eduma.com